OnPrem AD (Active Directory)
Overview
Active Directory (AD) is a directory service developed by Microsoft that provides a centralized location for managing and organizing information about network resources, including users, computers, and other devices. In this article, you will learn how to configure an Active Directory data source in Settings. The four main steps for this process are: Data Source Info, Account Types, and Sync Accounts.
Data Source Info
This is the first step that you need to fill in. There are three sections, About, Configuration, and Verification.
About
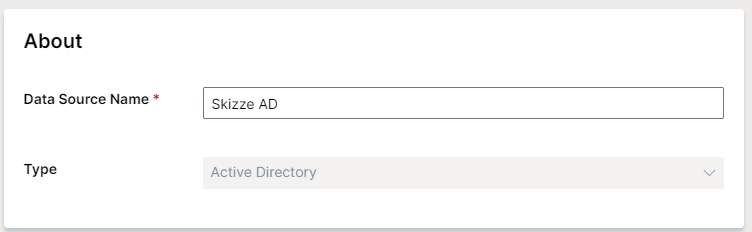
- Name your data source
- Select the Type drop-down menu
Configuration
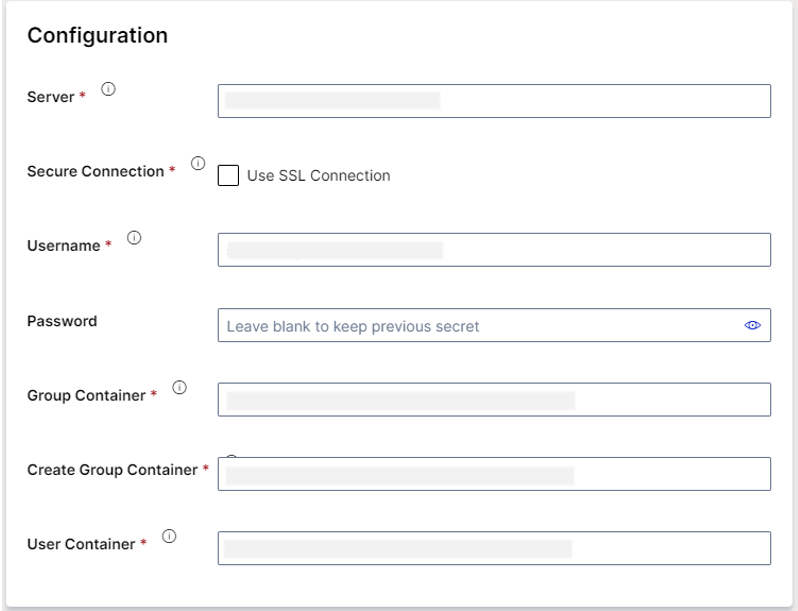
- Server
The IP address or the Domain of your Active Directory. You may optionally provide a specific port by appending a colon and port number.
Examples:
organisation.internal
10.0.0.2
organisation.internal:636
10.0.0.2:389
- Secure Connection
Enforce the connection from Apporetum to utilise LDAPS. Note that this will overwrite the LDAPS port if specified.
- Username
The username of a service principal object in Active Directory. This can be a sAmAccount Name or UserPrincipleName.
Examples:
<serviceAccount@organisation.com>
organisation\serviceAccount
- Password
The password of the service account. Please note that the field will be blank, but there will be a password protected in the Apporetum Password Vault. If you leave the field blank, this vault password will be retained. If you type into this field, it will be overwritten with the new entry you type.
- Group Container
Specifiy the Distinguished Name (DN) for an Org Unit (OU) or Domain Controller (DC) which Apporetum will use as the root container to discover groups. Can be a specific OU or the entire DC. Ensure that all groups which you would like to adopt is a child of this DN.
Examples:
DC=organisation,DC=internal
OU=OrgApps,DC=organisation,DC=internal
OU=AU,OU=Apps,DC=organisation,DC=internal
- Create Group Container
Specify the Distinguished Name (DN) for an Org Unit (OU) or Domain Controller (DC) which Apporetum will use as the parent container for new security groups. Can be a specific OU or the entire DC. Ensure Apporetum has write permissions the the member of this group. This is the location where Apporetum will create New security Groups.
Examples:
DC=organisation,DC=internal
OU=ApporetumGeneratedGroups,DC=organisation,DC=internal
OU=Apporetum,OU=AU,OU=Apps,DC=organisation,DC=internal
- User Container
Specify the Distinguished Name (DN) for an Org Unit (OU) or Domain Controller (DC) that Apporetum will use as the parent container for new groups. Can be a specific OU or the entire DC. This is a location where Apporetum will look for users when syncing accounts.
Examples:
DC=organisation,DC=internal
OU=ApporetumGeneratedGroups,DC=organisation,DC=internal
OU=Apporetum,OU=AU,OU=Apps,DC=organisation,DC=internal
Verification
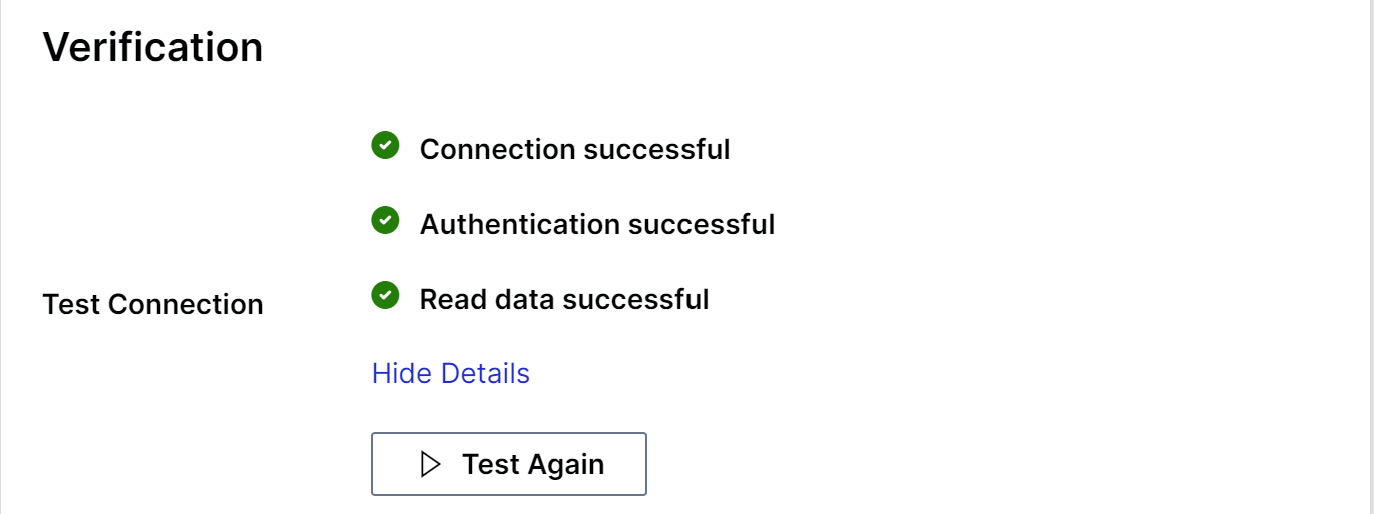
- Click Save and Test to run tests on Connection, Authentication, and Read Data
The tests will run in the following order: connection, authentication, read data. If one fails, the next test will not run. ::: 2. Click Show Details to see the reasons why tests failed. 3. Click Test Again once you have made any adjustments
Please contact Apporetum team for further help if needed.
Account Types
Click here to view detailed information on understanding account type, and creating or updating account type.
Excluded accounts are the accounts that are not part of any account type. They are not managed by Apporetum. They can't be added as the roles of either app manager or console user to manage Apporetum.
Sync Accounts
Click here to view detailed information on sync accounts.